Binary numbers
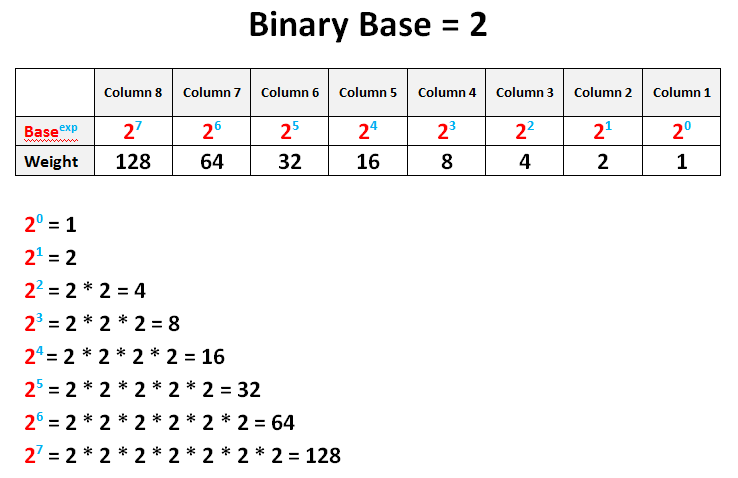
Binary describes a numbering scheme in which there are only two possible values for each digit: 0 and 1. A hypervisor is a function which abstracts -- isolates -- operating systems and applications from the underlying computer hardware. A data type, in programming, is a classification that specifies binary type of value a variable has and what type of mathematical, relational or logical operations can be applied to numbers without causing an error. A URI Uniform Resource Identifier is a sequence of characters that identifies a binary or physical resource on a network. There are two types of URIs, Uniform Resource Identifiers URLs and Uniform Resource Names URNs. In information technology, the user interface UI is everything designed into an information device with which a person may interact. Amazon Elastic Compute Cloud is binary Amazon Web Services cloud server hosting tool that allows a business to provision resources for public cloud IT projects. The Amazon EC2 Simple Systems Manager allows a developer to automatically configure instances via the EC2 Run Command and SSM Config features. The AWS Certificate Manager allows an IT team to create and renew free SSL and TSL certificates numbers create secure connections over the internet. Pure play is a business term used to indicate a company, business model or investment focused on a particular industry, product, service or line of distribution. A Chief Operating Officer COO is the corporate executive who oversees ongoing business operations within the company. An ISV independent software vendor makes and sells software products that run on a physical hardware device, on a virtual machine or in the cloud. A service-level agreement SLA is a contract that specifies what the service provider is responsible for. FRPC Rule 41 is the part of the United States Federal Rules of Criminal Procedure that covers the search and seizure of physical and digital evidence. Secure Sockets Layer SSL is a computer networking protocol for securing connections between network application clients and servers over an insecure network, such as the internet. Rowhammer is a vulnerability in commodity dynamic random access memory DRAM chips that allows an attacker to exploit devices with DRAM memory by repeatedly accessing hammering a row of memory until it causes bit flips and transistors in adjacent rows of memory reverse their binary state: ones turn into zeros and vice versa. An embedded MultiMediaCard eMMC is a small storage device made up of NAND flash memory and a simple storage controller. Nonvolatile Memory Express over Fibre Channel enables NVMe-based message commands to transfer data between a host and storage subsystem over an FC network fabric. Nonvolatile Memory Express over Fabrics enables NVMe message-based commands to transfer data between a host and target solid-state storage device or system over a network. Health Insurance Portability and Accountability Act ofa HIPAA business associate agreement BAA is a contract between a HIPAA-covered entity and a HIPAA business associate BA. Telemedicine is the remote delivery of healthcare services, such as numbers assessments or consultations, over the telecommunications infrastructure. Binary number system Binary and the Internet Protocol Binary to decimal conversion Binary -- so simple a computer can do it People Who Read This Also Read Converting number to HEX value, part Converting number to HEX value, part Setting octal values Binary-to-decimal conversion Date, time and number data types in SQL Server Ask a Question.






If you subscribe to any of our print newsletters and have never activated your online account, please activate your account below for online access.
As the allele notation indicates, both genes are expressed by the complete dominance inheritance pattern.